The US Department of Defense Inspector General found numerous security failings at the data centers and networks supporting the Ballistic Missile Defense System (BMDS).
In a report published earlier this year and made public this month, the Inspector General investigated a nonstatistical sample of 5 out of 104 DoD locations, across four military installations that manage BMDS elements and technical information.
Several elements of the report have been redacted for national security reasons, including the locations of the sites, but a separate letter from February notes: "We will perform the audit at DoD facilities where Ballistic Missile Defense System technical information is stored, processed, and transmitted, including the Missile Defense Agency Chief Information Office, Colorado Springs, Colorado and Missile Defense Agency testing facilities, Huntsville, Alabama.
"We will also visit select locations that support the Ground-Based Interceptor, Aegis Ballistic Missile Defense, and the Terminal High Altitude Area Defense elements of the Ballistic Missile Defense System."
The results of the visits were less than comforting.
Missile Defenseless
"The disclosure of technical details could allow US adversaries to circumvent the BMDS capabilities, leaving the United States vulnerable to deadly missile attacks," the report warns.
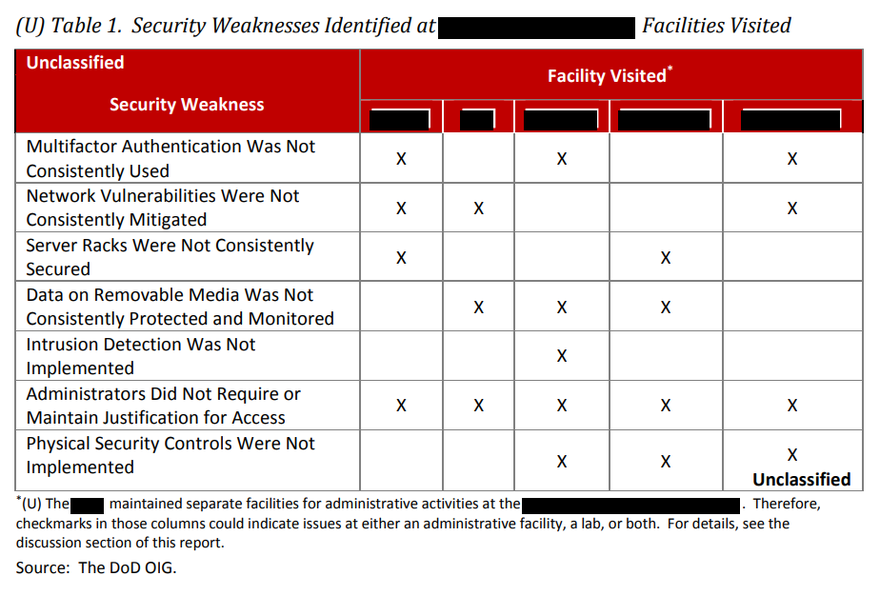
At each site, the Inspector General found numerous "systemic" security failings - for example, employees with access to the BMDS network in three of the five locations have yet to enable multi-factor authentication, a simple security technique widely used by the banking sector and many businesses. At one site, investigators found that "34 users accessed the [redacted] using single-factor authentication well past 14 business days, with some users not using CACs [Common Access Cards] to access the [redacted] for up to seven years."
Three of the five locations did not regularly apply patches for known security vulnerabilities across desktops, thin clients, support servers, domain controllers, backup servers, and security databases.
In March 2018, one of the bases was found to be susceptible to vulnerabilities classified as 'high' and 'critical,' disclosed way back in January. The vulnerabilities, "if exploited by unauthorized users, would likely result in privileged access to servers and information systems," the report warns. Another vulnerability at the same site had been identified in 2013, but was still not patched by the time of review.
Similar failings were found at the other sites - with perhaps the worst being an unpatched vulnerability that "was initially identified in 1990." The report notes: "The NIST assessment of this vulnerability concluded that it could be exploited multiple times by an attacker, and that the vulnerability could [redacted].
In July, the DoD's CIO said that "countless cyber incident reports show that the overwhelming majority of incidents are preventable by implementing basic cyber hygiene and data safeguards, which include regularly patching known vulnerabilities."
Physical security
Further failings were discovered with the data centers' physical security, with server racks routinely left unlocked. "In addition, the [redacted] data center manager did not control the server rack keys. NIST SP 800-53 requires organizations to secure keys, combinations, and other physical devices. In addition, the Defense Information Systems Agency Network Infrastructure Security Technical Implementation Guide requires all network infrastructure devices to be located in a secure room with limited access, and DoD Components to physically secure network devices using locked cabinets."
The site's data center manager told the investigators that they were not "aware of the requirement to secure the server racks and keys, but considered the existing security protocols to be sufficient because the [redacted] limited who had access to the data center."
Elsewhere, investigators "found an unlocked server rack despite a posted sign on the rack stating that the server door must remain locked at all times."
Such oversights could be dangerous, the Inspector General said, as "failing to keep server racks locked increases the risk that unauthorized individuals could access or tamper with servers that support network operations... The insider threat risk necessitates that organizations implement controls, such as locking server racks and controlling the keys to the server racks, to reduce the risk of malicious personnel manipulating a server’s ability to function as intended and compromising sensitive and classified data as well as the integrity and availability of the networks and systems."
At one location, officials "did not repair a known security issue with one of the facility’s doors." As a result, the door's sensor showed that the door was closed and the security sensor engaged, when it was not. The security site lead said that the sensors had been a problem for about four years.
"During our site visit, we observed security footage showing that a representative from the [redacted] gained unauthorized access to the [redacted] facility by simply pulling the door open. The security camera footage also showed that although the representative stopped to ask for directions, the individual she stopped did not request to see her [redacted] badge or question her facility access."
Issues with security cameras are also mentioned, but are mostly redacted. The document appears to focus on surveillance coverage, which was lacking, and storage of recordings, which was insufficient.
Encryption
Yet another problem raised was that of unencrypted removable media, which was apparently in common use, despite NIST SP 800-53 requiring organizations "to use cryptographic mechanisms such as hash totals and checksums to prevent unauthorized disclosure and modification of information," as well as a DoD CIO memorandum requiring DoD Components to encrypt sensitive data stored on removable media - issued way back in 2007. The Committee on National Security Systems Directive 504 also requires Federal agencies to encrypt removable media.
A security manager at one site said that less than one percent of Controlled Unclassified Information stored on removable media was encrypted. A security manager - not clear if the same one - said that data was not encrypted because they "used legacy systems that lacked the capability and bandwidth to encrypt data, did not have the resources to purchase encryption software, and used encryption software that did not always align with DoD encryption software."
The issues with removable media did not end there - "officials did not have controls in place to monitor the type and volume of classified data personnel downloaded to removable media," in contravention of The Committee on National Security Systems Directive 504.
"According to [redacted] officials, administrators did not have the capability to record and monitor the volume of data personnel downloaded from their networks to removable media," a problem that, if left unfixed, will mean networks are "at increased risk of not protecting sensitive and classified BMDS technical information from malicious users attempting to exfiltrate data that is critical to national security."
Monitoring
There's more: "Network administrators did not implement intrusion detection and prevention technology to restrict, block, and monitor suspicious network activities on their classified networks."
This is a requirement under Chairman of the Joint Chiefs of Staff Instruction 6510.01F, while NIST SP 800-94 requires Federal agencies to use multiple intrusion detection and prevention systems. "However, the [redacted] administrators stated that the [redacted] (network security device) used to protect the classified network lacked sufficient capacity (the amount of data that is able to be processed through a system) to support required intrusion detection and prevention configuration settings."
And finally, administrators at some sites "did not consistently require or maintain written justification as a condition for granting access to their networks and systems." As a result, administrators struggled to "validate whether access was granted appropriately."
The next step
The report details the various recommendations it has for the BMDS network - namely, to fix the issues by following the law. However, those involved "did not respond to the recommendation in the draft report. Therefore, the recommendation is unresolved. We request that the Director, Commanding General, and Commander provide comments on the final report."