A penetration tester was able to break into a data center via a hidden corridor he found on publicly-accessible building plans.
In a series of tweets this week, penetration tester Andrew Tierney, known as CyberGibbons, revealed how he once broke into a data center via plumbing engineer corridors behind the toilets.
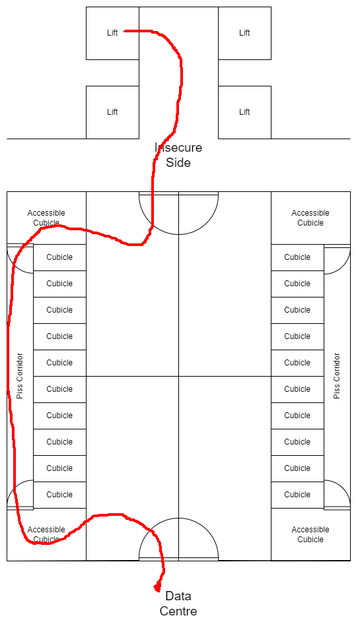
“I needed to gain access from the less-secure side of a sub-basement floor to the more-secure side,” he said. “By studying the floor plans of the building, I could see what I ended up calling the 'piss corridor' running along the back of the toilets.”
Tierney noted that in buildings with concealed cisterns, rooms can be designed with either panels that fold or a small corridor along the back side for easy access by plumbers. In the pen test in question, the building had been built using the corridor method.
“After gaining access to the insecure side, I entered the toilets. Via the accessible cubicle, there was a concealed door into the piss corridor. I opened it, walked along, minding my own business,” he said. “After *really* making sure there wasn't someone else in the other accessible cubicle, I let myself out. And I'm in the toilets on the secure side, in the data center.”
While such pen-tests can make amusing anecdotes, they can also show defects in data center design and security.
In this instance, the toilet corridor bypassed cylinder man-trap gates, and was discovered on publicly accessible planning documents. DCD has contacted Tierney for further details.
While penetration testers are there to highlight security flaws, an actual threat actor gaining access in such a way could lead to stolen data, compromised systems, or potential hardware theft/destruction.