A new form of malware that targets high-performance computing clusters has been discovered by security firm Eset. Despite its sophistication and targeted nature, it's currently unclear what the goals of the malware might be.
Named Kobalos, Eset says the malware is portable to multiple operating systems, including Linux, BSD, Solaris, and possibly AIX and Windows.
ESET says it hasn’t been able to determine the goals of the Kobalos operators as it hasn’t been able to capture network traffic of the malware in action. The malware is known to steal credentials in order to propagate, and the compromised machine gives threat actors the ability to read and write any files on the file system, but doesn’t mine cryptocurrency or perform other computationally heavy tasks on infected machines.
“We have not found any clues to indicate whether they steal confidential information, pursue monetary gain, or are after something else,” the company explains in a paper detailing the malware.
Opinion: Getting your security budget right
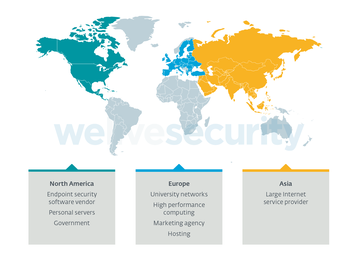
The company says it has discovered compromised university networks, HPC clusters, and hosting providers in Europe, as well as other victims in the US and Asia, but hasn’t revealed the scale of the issue. It did say, however, the “very limited number” of victims suggests a highly targeted campaign given the sophistication of the malware.
“Targets...tend to be high-performance computers and servers that are part of academic and research networks. One of the HPCs has no less than 512GB of RAM and almost a petabyte of storage,” the company said in its paper. “It is not clear why the HPC community is overly represented among the victims of these attacks. HPC centers are obviously interesting targets but typically less easily accessible than other academic servers.”
Kobalos the small but tricky malware
In Greek mythology, a Kobalos is a small, mischievous creature. Eset chose this name for the new malware given its ‘code size and many tricks.’ The x86-64 samples of the malicious code are only 25Kb in size.
“The way Kobalos is tightly contained in a single function and the usage of an existing open port to reach Kobalos makes this threat harder to find,” Eset said in a blog post detailing the malware. “This level of sophistication is only rarely seen in Linux malware. Given that it’s more advanced than the average and that it compromised rather large organizations, Kobalos may be running around for a little while.”
Kobalos grants remote access to the file system, provides threat actors the ability to spawn terminal sessions, and allows proxying connections to other Kobalos-infected servers. There are multiple methods for operators to reach a Kobalos-infected machine, but the most common was via embedding in an OpenSSH server executable (sshd).
Opinion: Measuring modern high-performance computing
Last year a number of supercomputers were compromised – including the University of Edinburgh’s Archer system – seemingly to use their computing power to mine cryptocurrencies. But Eset, the CERN Computer Security Team, and other organizations involved in mitigating attacks on scientific research networks say Kobalos malware predates those other incidents and currently has no link to the use of cryptocurrency malware.
It is currently unclear how long Kobalos has been active for. Eset said it found code strings related to Windows 3.11 and Windows 95, suggesting potential Windows-variant predecessors from the 1990s, but were unable to find any evidence of compromises prior to 2019.
Kobalos is not exclusively targeting HPCs. Eset reports that other victims include a large Asian ISP, a North American endpoint security vendor, as well as some personal servers.
Indicators of compromise for Kobalos are available on Eset’s Github page.