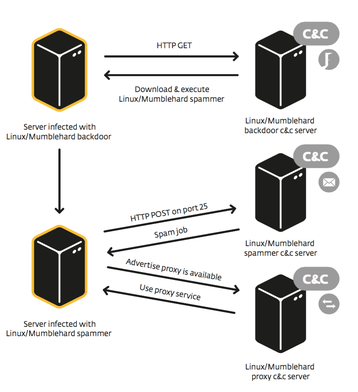
Researchers at Slovakia-based IT security firm ESET have discovered a malware family targeting web servers running Linux and BDS operating systems. The company’s analysis estimates that the malware – which it calls Mumblehard – has been infecting vulnerable systems for more than five years without detection.
“Among the compromised machines, web servers are the most susceptible to being infected,” the company wrote in a white paper summarizing the threat. When infected by Mumblehard, compromised servers open a backdoor to the attackers in control of the botnet, providing full control over the system. It also allows them to use infected servers to send out spam messages.
“Monitoring of the botnet suggests that the main purpose of Mumblehard seems to be to send spam messages by sheltering behind the reputation of the legitimate IP addresses of the infected machines,” wrote Marc-Etienne Levéillé, an ESET researcher, in the company’s security blog.
Levéillé said the threat is not your average piece of malicious code. The malware has two components, as he described – a backdoor to infect systems, and a spamming daemon. Both components are written in the Perl programming language, he observed, and feature identical customer packers written in assembly language. “The use of assembly language to produce ELF binaries so as to obfuscate the Perl source code shows a level of sophistication that’s higher than average,” Levéillé concluded.
Researchers at the company were able to register a domain name used by one of the botnet’s command and control servers – effectively establishing what security researchers call a “sinkhole” or “honeypot.” They observed 3000 machines infected during the first week of April, and more than 8,800 IP addresses were directed to their research sinkhole during a seven-month period. The size of the botnet doubled over the research period, the analysis noted.
Because the malware is written in Perl, Mumblehard is theoretically multi-platform. However, as ESET observed, there are limitations that limit it to Linux, FreeBSD, and perhaps Windows.
“The use of EWOULDBLOCK and EINPROGRESS constants in Mumblehard is nonportable. Nonetheless, Mumblehard defines the constants for Linux, FreeBSD and Windows, enabling the Perl script to run on these major systems,” noted the white paper analysis. “Although the ELF binary will not load on Windows, it’s possible that the malware is used without the packer or with a different packer for this platform.”
Links to DirectMailer
ESET’s research shows a “strong link” between the Mumblehard malware and Yellsoft – a provider of bulk mailing software used for marketing. The program it identifies is DirectMailer, which is also written in Perl. The strongest evidence linking the two, ESET noted, is readily available pirated copies of DirectMailer available online that “silently install the Mumblehard backdoor when run.”
Legitimate versions of DirectMailer are sold for $240 by Yellsoft on its website.
Most of the spam ESET has observed sent out by Mumblehard-infected machines markets online drug stores – including the popular spam lure of erectile dysfunction drugs.
“It is unclear if spamming is the only goal of this group. In theory, it is possible for the cybercriminals to deploy other executable files to thousands of servers at once,” ESET’s Levéillé said in the paper’s final analysis, adding the following rhetorical: “Is a pharmaceutical online store lucrative enough to justify the effort?”